What is BAS & how to lodge it online?
Everything you need to know about BAS and how Reckon One can help.
What is BAS?
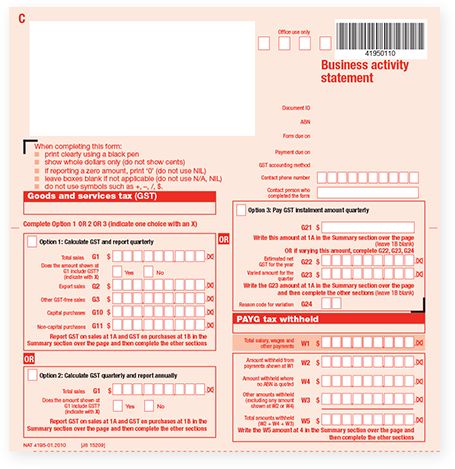
A Business Activity Statement (BAS) is a form that businesses must submit to the Australian Taxation Office (ATO) in order to report and pay their tax liabilities. A large part of BAS is related to GST.
Your BAS can also include PAYG withholding and instalments, wine equalisation tax, fuel tax credit and fringe benefit tax if these apply to your business.
How does BAS relate to GST?
When you complete a BAS form you are essentially reporting the goods and services tax amount you’ve collected on your sales minus any that you’ve paid on your purchases, with the difference being your refund or what you owe to the ATO.
For example:
- Your business charges $50 for your goods or services so your customer will be charged $55. The additional $5 is the GST that needs to be paid to the ATO.
- Your business buys supplies, you will be charged 10% in GST which you can claim back from the ATO as a credit.

Who has to lodge a BAS statement online?
If your small business is registered for GST you need to lodge a Business Activity Statement.
You must register for GST if:
- Your business has a GST turnover (gross income minus GST) of $75,000 or more per financial year
- Your non-profit organisation has a GST turnover of $150,000 or more per financial year
- You are a taxi driver and ride-sharing driver no matter what your turnover is
BAS lodgement due dates
If your business has a turnover of $20 million or less you can choose to lodge monthly or quarterly (over $20 million must report monthly).
| Monthly | Lodgement date |
|---|---|
| January - December | 21st of the following month |
| Quarterly | Lodgement date |
| July, August and September | 28 October |
| October, November and December | 28 February |
| January, February and March | 28 April |
| April, May and June | 28 July |


Choosing a method to complete your BAS Statement
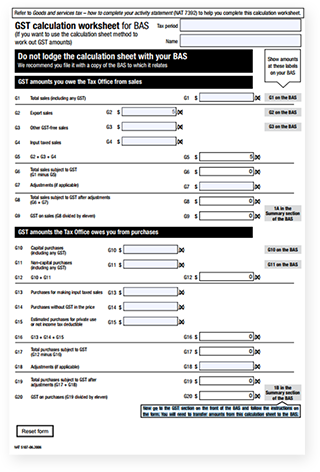
There are two methods that are offered by the ATO to work out your GST:
- Calculation worksheet method
- Accounts method
The method you choose to complete and submit your BAS will depend on your business size, complexity, accounting skills, the time you can allocate to BAS preparation, and personal preferences.
Identifying your accounting basis to complete a BAS Statement
Accrual or cash basis? There’s a few accounting basis decisions you’ll need to make to undertake your BAS and general accounting. The way you choose to do your accounting will also come into play when you submit your regular BAS.

GST calculation worksheet & BAS Statement Example
How to do a BAS statement
There are three main steps to completing your BAS:
Reckon makes lodging your BAS easy
Run the Reckon One “Activity Statement (BAS)” report that will help you generate the exact figures to enter onto your business activity statement form. Save and mark as lodged to help you stay organised. All Reckon accounting products are Simpler BAS enabled including Reckon One.

Download our free Business Activity Statements guide
This guide will lead you through everything you need to know about BAS, how it works, what it includes, how to complete it, and when you should submit.
Try Reckon for free.
Take control of your finances and keep track of receipts, payments, and GST.